Certificate based authentication
Use certificate based authentication with client certificates
If you already have a CA you could provide goshs with the CA certificate and this will activate certificate based authentication. Any certificate that is signed by the CA can now be used to authenticate against the server.
You will need to combine this option with TLS in any form to work. So choose -sand then either:
-ss-sk/-sc/-p12sl
See Transport Layer Security (TLS) / HTTPS for details.
Usage example
$ goshs -s -p12 server/goshs.p12 -ca ca/ca.crt
INFO [2024-07-04 18:01:46] Download embedded file at: /example.txt?embedded
INFO [2024-07-04 18:01:46] Download embedded file at: /test?embedded
Enter password for server/goshs.p12:
INFO [2024-07-04 18:01:46] Using certificate auth with ca certificate: ca/ca.crt
INFO [2024-07-04 18:01:46] Serving on interface eth0 bound to 10.137.0.27:8000
INFO [2024-07-04 18:01:46] Serving on interface lo bound to 127.0.0.1:8000
INFO [2024-07-04 18:01:46] Serving HTTPS from /home/user with ssl enabled server key: , server cert: , server p12: server/goshs.p12
INFO [2024-07-04 18:01:46] You provided a certificate and might want to check the fingerprint nonetheless
INFO [2024-07-04 18:01:46] SHA-256 Fingerprint: 69 69 49 1A BE 4E 4D 00 37 B9 3E 6F 40 EF C8 DD 81 8F 69 18 C1 07 39 BC 3E 0F B2 43 C8 2D 7B 01
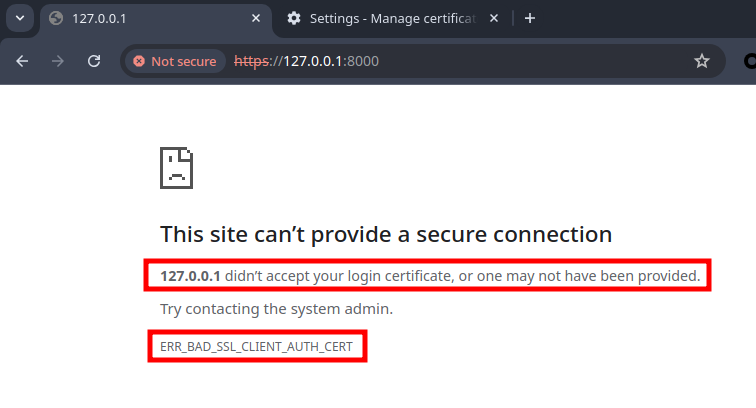
INFO [2024-07-04 18:01:46] SHA-1 Fingerprint: 0B 39 8E CA 16 E5 F3 EA 86 E5 7D B2 31 8F 7D C8 28 8D 42 E2 This screenshot shows the browser without providing a valid certificate.
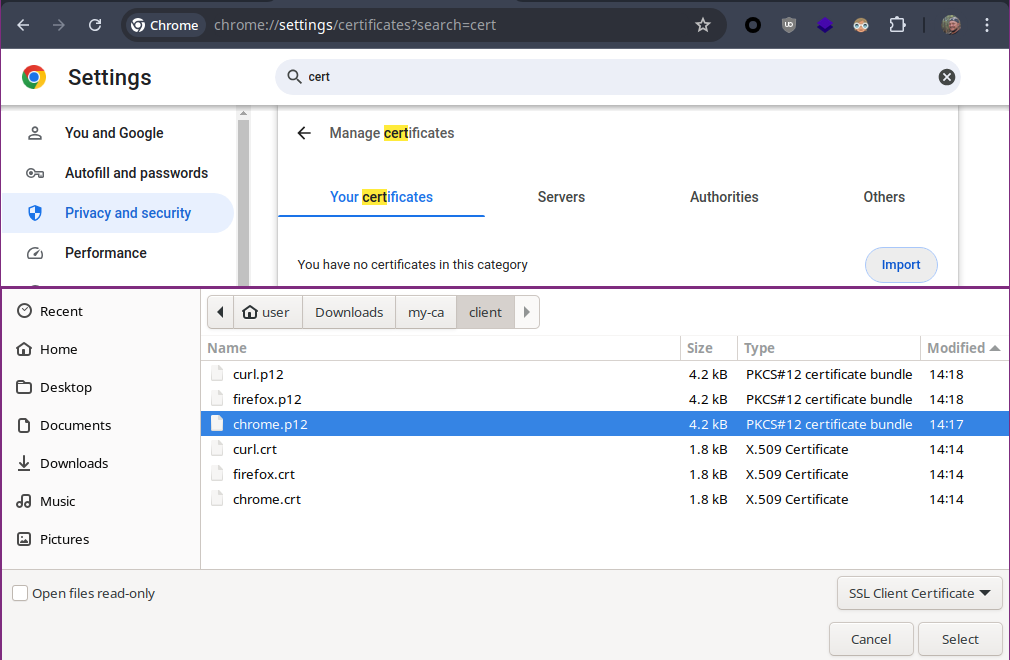
Importing the valid certificate into the certificate store in Chrome.
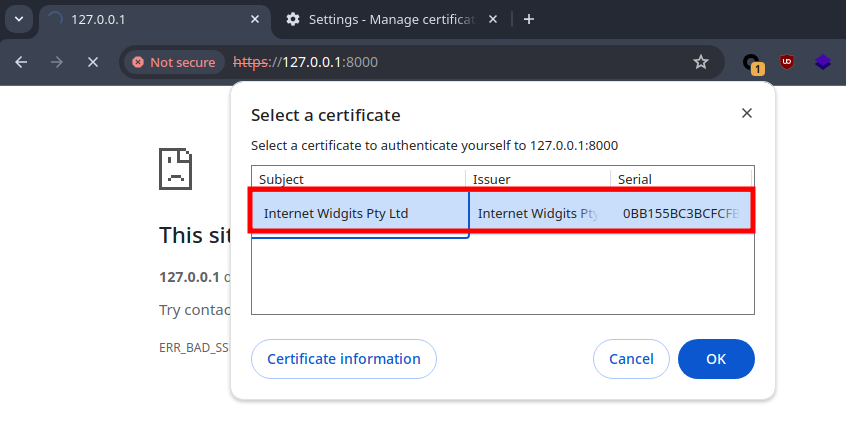
Reloading the page will let you choose the valid certificate.
And then you will have authenticated access to the goshs instance. The same goes for firefox or even for curl:
$ curl -skIL https://localhost:8000vs
$ curl -skIL --cert-type p12 --cert curl.p12 https://localhost:8000
HTTP/2 200
content-type: text/html; charset=utf-8
date: Thu, 7 Jul 2024 12:53:53 GMTExample CA Setup
You can use basically any you already created and just need to provide goshs with the CA certificate. But to give you an example here is, how I created the CA for this example: